🕒 4 min read
I have spent decades working with confidential systems, privileged credentials, financial platforms, healthcare data, and enterprise-grade infrastructure. Over the years, I’ve been entrusted with access to environments where a single compromise could create cascading damage. This reality alone renders a casual approach to security unacceptable.
My personal security stack is deliberate and layered. I use unique 40‑character passwords for every service, enforced through a password manager. Every critical system requires two‑factor authentication (2FA). And I route traffic through a VPN at all times—whether I’m at home, in an airport, or on a café Wi‑Fi network.
Those three controls—long, unique passwords, mandatory 2FA, and encrypted tunneling—already place my security posture far above the average user. But over time, I realized something important: relying solely on commercial VPN providers introduced trust assumptions I wasn’t fully comfortable with. That realization led me to build my own VPN server while still using a hardened, well‑maintained commercial client (WireGuard) to connect to it.
What a VPN Actually Protects (and Why It Matters)
A VPN is not magic. It does not make you anonymous, invisible, or immune to mistakes. What it does is very specific—and very powerful.
- Encrypts traffic between your device and a trusted endpoint
- Prevents Wi‑Fi eavesdropping and packet sniffing
- Blocks man‑in‑the‑middle attacks on untrusted networks
- Reduces exposure to IP‑based tracking and profiling
- Ensures DNS requests are not trivially observed or altered
Without a VPN, every open or poorly secured network becomes a liability. Attackers don’t need advanced exploits—they just need proximity and patience.
Why I Built My Own VPN Instead of Fully Trusting a Provider
Commercial VPNs solve many problems, but they also introduce a central question: who do you trust with your traffic?
When you use a third‑party VPN, you are shifting trust from your ISP to the VPN provider. That provider may claim “no logs,” but claims are not controls. Jurisdiction, logging policies, infrastructure visibility, and key management all matter.
By building my own VPN server, I gained:
- Full control over encryption keys and rotation
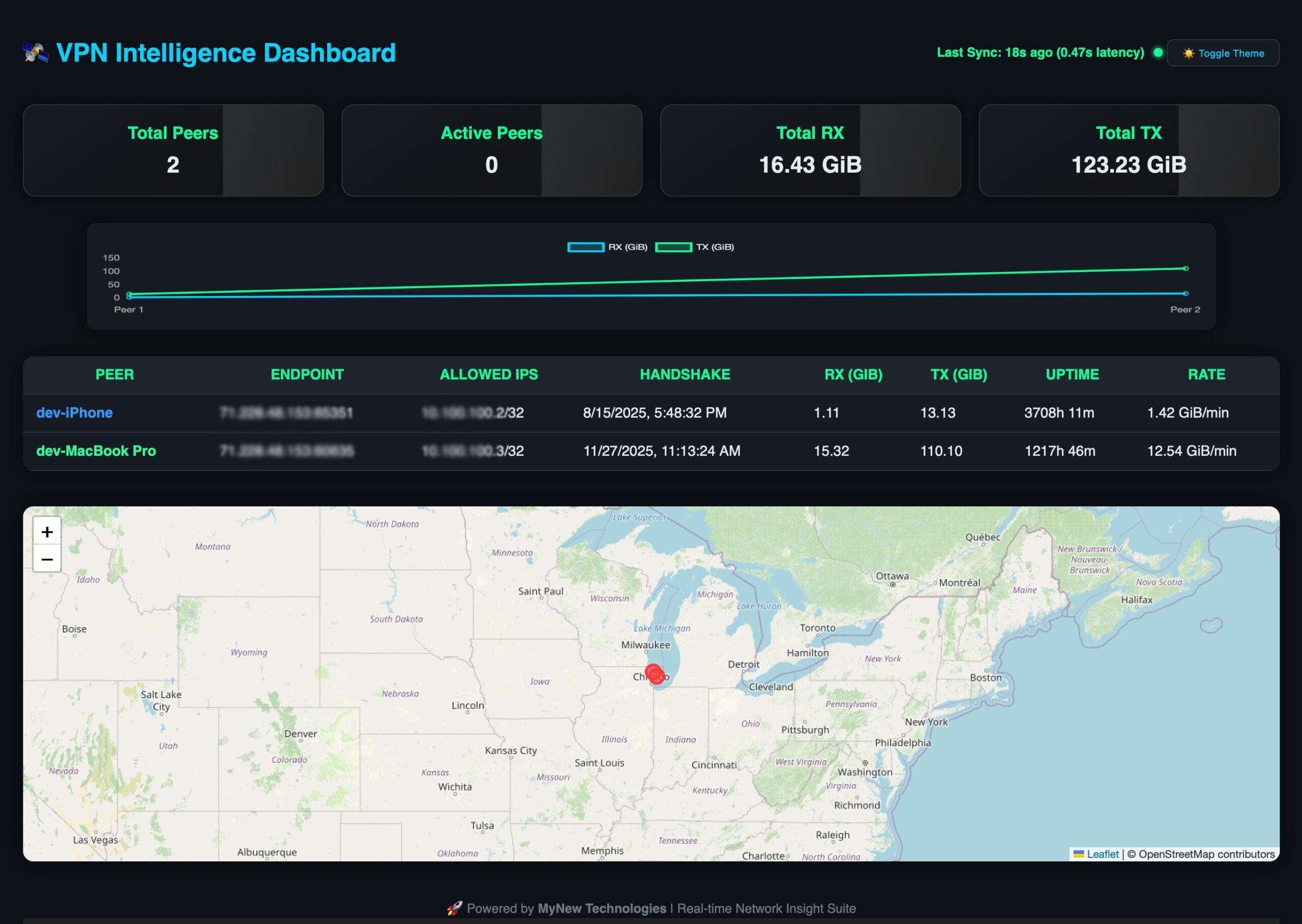
- Visibility into every peer and handshake
- No third‑party traffic aggregation
- Predictable performance and routing
- Auditability of logs and telemetry
I still use a commercial, battle‑tested client (WireGuard) because security is not about reinventing cryptography—it’s about correctly implementing proven tools.
Security Rating: How Strong Is This Setup?
Based on modern threat models, this configuration rates exceptionally high for an individual practitioner.
- Password Hygiene: Excellent (unique, long, non‑reused)
- Authentication: Excellent (mandatory 2FA)
- Network Protection: Excellent (always‑on VPN)
- Trust Boundary Control: Excellent (self‑hosted VPN)
My personal overall rating: 9.5 / 10. The remaining 0.5 is reserved for operational discipline—patching cadence, endpoint hardening, and behavioral awareness.
Recommended upgrades include hardware security keys (FIDO2), DNS‑over‑HTTPS enforcement, and endpoint disk encryption with secure boot.
Pros and Cons of Using a VPN
Pros
- Encrypts traffic on hostile networks
- Protects credentials in transit
- Reduces ISP and Wi‑Fi tracking
- Enables secure remote access
Cons
- Can introduce latency
- Requires trust in infrastructure
- Misconfiguration can reduce security
- False sense of anonymity if misunderstood
Why Many Users Don’t Use a VPN
Most users don’t ignore VPNs out of recklessness—they ignore them out of misunderstanding. Security failures are invisible until they are catastrophic. Eventually, convenience loses.
VPNs are often marketed as privacy tools rather than risk‑reduction tools. When people don’t understand the threat model, they don’t perceive value.
Top VPN Services for 2026
- Mullvad
- Proton VPN
- IVPN
- NordVPN (enterprise features)
- Cloudflare WARP (specific use cases)
What Can Happen If You Don’t Use a VPN
- Credential theft on public Wi‑Fi
- Session hijacking
- DNS spoofing and malicious redirects
- Silent traffic interception
- Corporate access compromise
None of these scenarios require advanced hackers. They require opportunity. A VPN removes that opportunity.
Final Thought
Building your own VPN is not for everyone. But understanding why it matters should be. Security is not about paranoia—it is about respect for the systems, people, and data you are responsible for protecting.